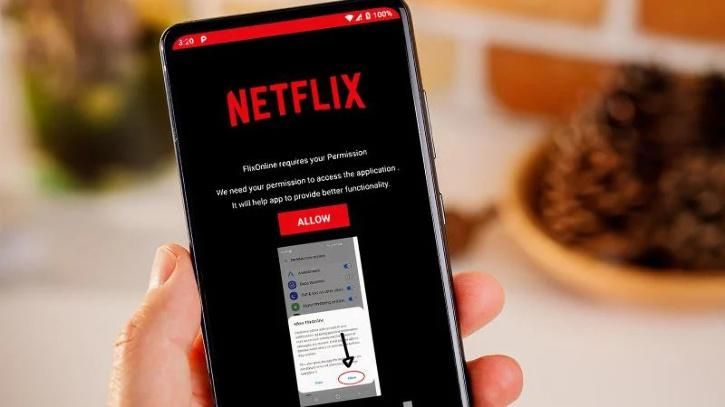
Malware aimed at the AWS Lambda Serverless Platform has been discovered for the first time.
A first-of-its-kind malware targeting Amazon Web Services' (AWS) Lambda serverless computing platform has been discovered in the wild.
In a move toward the metaverse, 3D adverts are now available on Facebook and Instagram.
Through a new agreement with an e-commerce technology startup, Meta Platforms Inc will make it easier for marketers to run three-dimensional ads on Facebook and Instagram.
Conti, Diavol Ransomware Access-Broker Ops: Google Blows the Lid Off
Exotic Lily, a full-time cybercriminal initial-access gang that utilizes phishing to penetrate businesses' networks for subsequent destructive behavior, has been discovered by researchers.
'Largest in the Country's History' describes the Cyberattacks against Israeli Government Sites.
Government websites were taken down as a result of DDoS assaults against Israeli telecom firms, prompting a short state of emergency.
10 Pieces of Tech You Really Don't Need Anymore and are Outdated
The are ancient and out of use , and you should think about saving up that space.
Hackers are starting to use TCP Middlebox Reflection as a weapon in DDoS attacks.
Six months after the unique attack method was disclosed in principle, distributed denial-of-service (DDoS) assaults exploiting a new amplification technique dubbed TCP Middlebox Reflection were discovered for the first time in the field.
Gems, the UAE's largest school group, has reported a cyber-attack; an inquiry has been initiated.
Gems Education revealed to Khaleej Times on Thursday that it had been the victim of a cyber-attack.
Hackers planted fraudulent digital evidence on the phones and computers of Indian activists and lawyers.
In an attempt to plant "incriminating digital evidence," a hitherto unknown hacking gang has been connected to targeted assaults against human rights activists, human rights defenders, professors, and attorneys across India.
Nooie baby monitors have zero-day vulnerabilities that might allow video stream hijacking
Attackers might use security flaws in Nooie baby monitors to get access to the video stream or execute malicious code on susceptible devices.
Data from the British Council has been leaked. 10,000 records of students
A public search engine indexed a blob container that had over 144,000 xml, json, and xls/xlsx files.
HPE and the UAE Cyber Security Council are collaborating to improve youth education.
HPE's early career program helps them realize their full potential and develop the core skills required for a successful career in the IT sector.
Fake Government Contracts from Cloned Department of Labor Site Hawks
A well-crafted but phony government procurement webpage invites bidders to make bids for lucrative government projects, but instead collects credentials.
Sophisticated Android and Windows Hacks Reveal Zero-Day Trove
Watering-hole attacks were carried out on two servers by 'experts' who exploited Chrome, Windows, and Android weaknesses.
Victims of the Google Voice Authentication Scam are still on the hook.
The FBI issued a notice this week because it is witnessing so much fraudulent Google Voice activity, where victims are linked to fake virtual phone numbers.
DLI wishes you a Very Happy New Year!
May this year bring new happiness, new goals, new achievements, and many new inspirations to your life
Top 7 common Cybersecurity Myths — Busted
Despite the increased awareness of cybersecurity, there are numerous myths about it. These misunderstandings might obstruct effective security.
2022: SaaS Security Meltdowns & Chronic Pain in Supply-Chain
The increasing web of connections between SaaS apps, allowing for automated corporate procedures – and widespread lateral movement by attackers, well beyond IT's control.
Why Are Your Employees at Risk of a Cyber Attack During the Holidays? (And How to Take Precautions)
While many people's thoughts are off work during the holidays, this is generally when cybercriminals organize their most sinister attacks.
Providing bulletproof hosting to cyber criminals led Russian man to a 60-month jail sentence.
Similar to regular web hosting, but it is far more permissive in terms of what may be hosted on its servers. They're notorious for offering safe havens for dangerous information and behavior, as well as ensuring threat actors' anonymity.
Spider-Man Movie Release Frenzy Bites Fans with Credit-Card Harvesting
Attackers are taking advantage of the hype around the release of the new Spider-Man film to steal bank information and spread malware.
@HACK debut edition will bring together the best hackers in the world.
The Event will run from 28th - 30th November in Riyadh.
3 key technologies to invest in to fight Ransomware
The number of ransomware victims has increased by 1,000%. Secure email, network segmentation, and sandboxing for protection are discussed by a cybersecurity researcher and practitioner at FortiGuard Labs.
Facebook is removing billions of records by shutting down its facial recognition system.
Meta announced plans to discontinue its decade-old "Face Recognition" system
Outbreak of the Pandemic lead to a wave of Cybersecurity threats in the Middle East
Due to investigations into cyberattacks on the UAE, the experts published 49 threat intelligence reports.
How to secure yourself against phishing attack
If it looks like a duck, swims like a duck, and quacks like a duck, it's definitely a duck, according to Tony Anscombe, Chief Security Evangelist at ESET. So, how can you use the duck test to protect yourself from phishing?
Hackers Could Have Stolen Cryptocurrency From Wallets Due to a Critical Flaw in OpenSea
Malicious actors might have utilized a now-patched major vulnerability in OpenSea, the world's largest non-fungible token (NFT) marketplace, to drain cryptocurrency money from a victim by delivering a specially-crafted token, providing a new attack channel for exploitation.
Faulty Router Configuration was liable for the Outage says Facebook
One easily disproved conspiracy theory linked the ~six-hour outage to a supposed data breach tied to a Sept. 22 hacker forum ad for 1.5B Facebook user records.
Minorities and Women are the most prone to being Hacked
According to a survey, income level, education, and being a member of a disadvantaged community all have a role in cybercrime consequences.
A new bug in Microsoft Windows might make it simple for hackers to install a rootkit.
Security researchers revealed an unpatched vulnerability in Microsoft's Windows Platform Binary Table (WPBT), which affects all Windows-based devices since Windows 8, and may be used to install a rootkit and compromise device integrity.
State-sponsored APTs may be exploiting a critical Zoho bug, according to CISA and the FBI
Since early August, a recently discovered problem in a Zoho single sign-on and password management product has been actively exploited.
Cybersecurity Trends and Tips
The following cybersecurity trends and suggestions provide some general principles that you can follow as an employee or a tech professional when surfing the web or utilizing the internet.
CISA and FBI: Watch out for ransomware attacks that may occur over the Labor Day weekend
The advisory recommends an important line of defense to reduce the risk posed by ransomware and other threats.
High End Nexus Gear has been issued for Critical Fixes by Cisco
Networking giant issues two critical patches and six high-severity patches.
$260 Million in Assests Stolen in the Biggest Crypto Heist returned by hacker saying; he is not interested in the money.
Over one-third of the $613 million in cryptocurrency stolen from blockchain platform Poly Network has been returned, with the hacker saying he did it for fun.
G20 ministers say 'Digital Transformations are set to play a key role in the world post pandemic.'
Al-Asheikh added that the COVID-19 pandemic is an opportunity to be seized, and “not just a passing crisis”
Why should businesses invest in cybersecurity? - the cost of cybercrime is on a rise.
Multifront war is what we now call modern day cybercrime battles.
Data Leak After Reported Cyber Ransom Confirmed by Saudi Aramco
After hackers purportedly requested a $50 million ransom from the world's most valuable oil exporter, Saudi Aramco revealed that some company files were exposed.
USBs are back: Rare, advanced threat campaign targets users
The Kaspersky Managed Detection and Response service can help identify and stop attacks in their early stages, before the attackers achieve their goals.
Ransomware Attack causes massive data loss to Guess Fashion Brand
More than 1,300 people had their information compromised during the ransomware attack, including account numbers, debit- and credit-card numbers, and even the related security codes, access codes and personal identification numbers.
Year-Long Cyber Espionage Campaign targets Oil & Gas
A global effort to steal information from energy companies is using sophisticated social engineering to deliver Agent Tesla and other RATs
A series of unfortunate events
Researchers accidentally release exploit code for new Windows ‘zero-day’ bug Print Nightmare
Research worker nets $30k when exposing users’ personal content
An ethical hacker has landed a $30,000 bug bounty payout after finding a security vulnerability in Instagram that potentially exposed users’ private content to nefarious actors.
Threat Actors Use Google Docs to Host Phishing Attacks
Exploit in the widely used document service leveraged to send malicious links that appear legitimate but actually steal victims credentials.
Stolen Data Points Collected in Billions by a Mysterious Custom Malware.
Anonymous malware led researchers to discover that a large number of files, credentials, cookies, and other data collected in the cloud database were stolen.
6M Gamer Profiles leaked through a Mobile Game.
Unprotected server exposes AMT Games user data containing user emails and purchase information.
Cybercrime Swamp transpired Threat Actors ‘Privateer’
‘Privateers’ aren’t necessarily state-sponsored, but they have some form of government protection while promoting their own financially-motivated criminal agenda, according to Cisco Talos.
Microsoft, Google Clouds Hijacked for Gobs of Phishing
Around 52M malicious messages in just Q1 2021
‘Scheme Flooding’- Websites Track Users Across Browsers.
A new and rising threat to cross-browser anonymity.
Fake COVID-19 Vaccine Phishing Website taken down by the federal Law.
‘Freevaccinecovax.org' pretended to be a biotech company, but it was actually gathering information from visitors for criminal purposes.
Multi-Gov Task Force Plans to Take Down the Ransomware Economy
A consolidation of 60 worldwide entities (counting the DoJ) has proposed a sweeping plan to chase down and disrupt ransomware gangs by going after their monetary operations.
It's common to fall victim to a cyberattack, but a VPN will assist you.
You might believe that cybercrime is more prevalent in countries where people are less tech savvy.
Securing your remote workforce
Canon EMEA Director of Information Security, shares his top 5 tips to protect yourself from cyberattacks.
Spread of Malware via WhatsApp by a fake Netflix app on Google Play.
Researchers discovered malware disguised as a Netflix app on the Google Play store that spread through WhatsApp messages.
Encryption’s vital role in GDPR Compliance
Data- viewed as a business-basic resource for associations, ought to be ensured against pernicious programmers searching for freedoms to take the information.
The Malware Used to Inject SolarWinds Backdoor has Been Unveiled
Called "Sunspot," the malignant tool adds to a growing list of previously disclosed malicious software such as Sunburst and Teardrop.
This sector witnessed a 45% Spike in Cyber Attacks Since Nov 2020
Cyberattacks targeting healthcare organizations have spiked by 45% since November 2020 as COVID-19 cases continue to increase globally.
Your Private Documents could have been compromised by the Hackers Bug
Google has patched a bug in its feedback tool incorporated across its services that could be exploited by an attacker to potentially steal screenshots of sensitive Google Docs documents simply by embedding them in a malicious website.
Microsoft Caught Up in SolarWinds Spy Effort, Joining Federal Agencies
Also referred to the Breach of the month. The ongoing, growing campaign is “effectively an attack on the United States and its government and other critical institutions,” Microsoft warned.
Ransomware and IP Theft: Top COVID-19 Healthcare Security Scares
From ransomware attacks that crippled hospitals, to espionage attacks targeting COVID-19 vaccine supply chain, Beau Woods discusses the top healthcare security risks.
Amnesia:33 TCP/IP Flaws Affect Millions of IoT Devices
A new set of vulnerabilities has been discovered affecting millions of routers and IoT and OT devices from more than 150 vendors, new research warns.
Changing Employee Security Behavior Takes More Than Simple Awareness
Designing a behavioral change program requires an audit of existing security practices and where the sticking points are.
Experts Weigh in on E-Commerce Security Amid Snowballing Threats
How a retail sector reeling from COVID-19 can lock down their online systems to prevent fraud during the upcoming holiday shopping spike.
How to Write a Cybersecurity Playbook During a Pandemic
If it feels like you’re constantly revising the draft of your cybersecurity playbook these days, it’s because you probably are.
Cisco Patches High-Severity Bugs Impacting Switches, Fibre Storage
Nine bugs were patched, eight of which are rated 'high' severity.
MFA Bypass Bugs Opened Microsoft 365 to Attack
Vulnerabilities ‘that have existed for years’ in WS-Trust could be exploited to attack other services such as Azure and Visual Studio.